How To Ssh To A Server From Windows
Introduction
Accessing machines remotely became a necessity a long time ago and we can barely imagine how it would exist if we couldn't command computers from remote locations. In that location are many ways to plant a connection with a remote car depending on the operating system you are running, just the two most used protocols are:
- Secure Beat (SSH) for Linux-based machines
- Remote Desktop Protocol (RDP) for Windows-based machines
The ii protocols utilize the client and server applications to found a remote connection. These tools allow y'all to gain admission and remotely manage other computers, transfer files, and do virtually anything you can practice while physically sitting in front end of the automobile.
Prerequisites
Before you can constitute a secure remote desktop protocol with a remote machine, there are a few bones requirements to run across:
- The remote computer must exist turned on at all times and have a network connectedness.
- The client and server applications need to be installed and enabled.
- Yous need the IP accost or the proper name of the remote machine you want to connect to.
- Y'all need to have the necessary permissions to access the remote estimator.
- Firewall settings need to permit the remote connection.
What is SSH?
Secure Beat, sometimes referred to as Secure Socket Shell, is a protocol which allows you to connect securely to a remote computer or a server by using a text-based interface.
When a secure SSH connection is established, a shell session will be started, and you lot will exist able to manipulate the server by typing commands within the client on your local computer.
System and network administrators use this protocol the virtually, too as anyone who needs to manage a computer remotely in a highly secure manner.
How Does SSH Work?
In order to found an SSH connection, you need two components: a client and the corresponding server-side component. An SSH client is an application you install on the computer which you will use to connect to some other figurer or a server. The customer uses the provided remote host information to initiate the connexion and if the credentials are verified, establishes the encrypted connection.
On the server'southward side, there is a component called an SSH daemon that is constantly listening to a specific TCP/IP port for possible customer connection requests. Once a client initiates a connectedness, the SSH daemon will reply with the software and the protocol versions it supports and the 2 will exchange their identification information. If the provided credentials are right, SSH creates a new session for the appropriate environment.
The default SSH protocol version for SSH server and SSH customer communication is version 2.
How to Enable an SSH Connection
Since creating an SSH connection requires both a client and a server component, yous need to make sure they are installed on the local and the remote machine, respectively. An open up source SSH tool—widely used for Linux distributions— is OpenSSH. Installing OpenSSH is relatively easy. It requires access to the concluding on the server and the calculator that yous use for connecting. Note that Ubuntu does not accept SSH server installed by default.
How to Install an OpenSSH Customer
Before you proceed with installing an SSH client, make sure it is not already installed. Many Linux distributions already have an SSH client. For Windows machines, you lot tin install PuTTY or whatsoever other client of your choice to proceeds access to a server.
To bank check if the client is bachelor on your Linux-based arrangement, y'all will need to:
- Load an SSH concluding. You can either search for "last" or printing CTRL + ALT + T on your keyboard.
- Type in
sshand press Enter in the terminal. - If the client is installed, you lot will receive a response that looks like this:
[electronic mail protected]:~$ ssh usage: ssh [-1246AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-east escape_char] [-F configfile] [-I pkcs11] [-i identity_file] [-J [[electronic mail protected]]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o pick] [-p port] [-Q query_option] [-R address] [-S ctl_path] [-West host:port] [-w local_tun[:remote_tun]] [[electronic mail protected]]hostname [command] [email protected]:~$ This ways that you are gear up to remotely connect to a physical or virtual car. Otherwise, you will have to install the OpenSSH customer:
- Run the following control to install the OpenSSH client on your computer:
sudo apt-get install openssh-customer - Blazon in your superuser countersign when asked.
- Hit Enter to complete the installation.
Y'all are now able to SSH into whatever machine with the server-side application on it, provided that you have the necessary privileges to gain access, as well as the hostname or IP address.
How to Install an OpenSSH Server
In order to accept SSH connections, a machine needs to have the server-side office of the SSH software toolkit.
If you start desire to check if OpenSSH server is bachelor on the Ubuntu organisation of the remote computer that needs to accept SSH connections, you tin can attempt to connect to the local host:
- Open the terminal on the server machine. You can either search for "last" or press CTRL + ALT + T on your keyboard.
- Type in
ssh localhostand hit enter. - For the systems without the SSH server installed the response volition expect similar to this:
[electronic mail protected]:~$ ssh localhost ssh: connect to host localhost port 22: Connection refused [email protected]:~$ If the above is the case, yous volition demand to install the OpenSSH server. Leave the last open and:
- Run the post-obit command to install the SSH server:
sudo apt-get install openssh-server ii. - Type in your superuser countersign when asked.
- Enterand Y to allow the installation to continue after the disk infinite prompt.
The required back up files volition be installed, and and then y'all can check if the SSH server is running on the machine by typing this control:
sudo service ssh condition The response in the final should expect similar to this if the SSH service is now running properly:
[electronic mail protected]:-$ sudo service ssh status • ssh.service - OpenBSD Secure Beat server Loaded: loaded (/lib/systemd/organisation/ssh.service; enabled; vendor preset: enab Active: active (running) since Fr 2018-03-12 10:53:44 CET; 1min 22s ago Process: 1174 ExecReload=/bin/kill -HUP $MAINPID (code=exited, status=0/SUCCES Main PID: 3165 (sshd) Another way to test if the OpenSSH server is installed properly and volition accept connections is to try running the ssh localhost command again in your terminal prompt. The response will look like to this screen when yous run the command for the start time:
[email protected]:~$ ssh localhost The actuality of host 'localhost (127.0.0.1)' tin't exist established. ECDSA central fingerprint is SHA256:9jqmhko9Yo1EQAS1QeNy9xKceHFG5F8W6kp7EX9U3Rs. Are you lot sure you desire to continue connecting (aye/no)? yes Warning: Permanently added 'localhost' (ECDSA) to the listing of known hosts. [email protected]:~$ Enter yes or y to continue.
Congratulations! You accept set upward your server to have SSH connexion requests from a unlike
calculator using an SSH client.
TIP
You can now edit the SSH daemon configuration file, for example, you can change the default port for SSH connections. In the terminal prompt, run this command:
sudo nano /etc/ssh/sshd_config The configuration file will open in the editor of your choice. In this case, nosotros used Nano.
If yous need to install Nano, run this command:
sudo apt-become install nano Please annotation that you need to restart SSH service every fourth dimension you make any changes to the sshd_config file by running this control:
sudo service ssh restart How to Connect via SSH
Now that you accept the OpenSSH customer and server installed on every machine you need, you tin can plant a secure remote connection with your servers. To do so:
- Open up the SSH terminal on your machine and run the following command:
ssh [email protected]_ip_addressIf the username on your local machine matches the one on the server you are trying to connect to, you lot tin can merely type:
ssh host_ip_addressAnd hit Enter. - Blazon in your password and hit Enter. Note that you volition not become any feedback on the screen while typing. If you are pasting your password, make certain it is stored safely and not in a text file.
- When you are connecting to a server for the very offset fourth dimension, information technology will ask yous if you want to continue connecting. Just blazon yes and hit Enter. This message appears only this time since the remote server is non identified on your local automobile.
- An ECDSA fundamental fingerprint is at present added and yous are connected to the remote server.
If the computer y'all are trying to remotely connect to is on the same network, and so it is all-time to use the private IP accost instead of the public IP address. Otherwise, you lot will have to use the public IP address only. Additionally, make certain that you know the correct TCP port OpenSSH is listening to for connection requests and that the port forwarding settings are correct. The default port is 22 if nobody inverse configuration in the sshd_config file. You may also just append the port number after the host IP accost.
Here is the example of a connection request using the OpenSSH client. We will specify the port number as well:
[email protected]:~$ ssh [email protected] –p7654 [email protected]'s password: The authenticity of host '185.52.53.222 (185.52.53.222)' can't be established. ECDSA key fingerprint is SHA256:9lyrpzo5Yo1EQAS2QeHy9xKceHFH8F8W6kp7EX2O3Ps. Are you lot certain you want to continue connecting (yes/no)? yes Alert: Permanently added ' 185.52.53.222' (ECDSA) to the listing of known hosts. [email protected]:~$ Y'all are now able to manage and command a remote car using your terminal. If y'all have trouble connecting to a remote server, make sure that:
- The IP address of the remote machine is correct.
- The port SSH daemon is listening to is non blocked by a firewall or forwarded incorrectly.
- Your username and password are correct.
- The SSH software is installed properly.
SSH Further Steps
Now that yous are able to establish a connection to your server using SSH, we highly recommend a few farther steps to improve SSH security. When y'all leave the setup with the default values, it is more than likely to be hacked and your server can easily become a target of scripted attacks.
Some of the suggestions for hardening SSH by editing the sshd configuration file include:
- Change the default TCP port where SSH daemon is listening. Modify it from 22 to something much higher, for case 24596. Make certain you do not employ a port number that is easy to gauge, such as 222, 2222 or 22222.
- Use SSH key pairs for authentication for passwordless SSH login. They are both safer and also permit logging in without the need to use your password (which is faster and more user-friendly).
- Disable countersign-based logins on your server. If your password gets croaky, this volition eliminate the possibility of using it to log into your servers. Before you disable the choice to log in using passwords, information technology is important to brand certain that authentication using key pairs is working properly.
- Disable root access to your server and use a regular account with the su – control to switch to a root user.
You can as well use TCP wrappers to restrict access to certain IP addresses or hostnames. Configure which host can connect using TCP wrappers by editing the /etc/hosts.allow and etc/hosts.deny files.
Note that immune hosts supersede the denied hosts. For case, to permit SSH admission to a unmarried host you will first deny all hosts by adding these two lines in the etc/hosts.deny:
sshd : ALL
ALL : ALL
Then, in the etc/hosts.allow add a line with the allowed hosts for the SSH service. That tin be a single IP accost, an IP range, or a hostname: sshd : ten.ten.0.five, LOCAL.
Make certain to keep your log in information secure at all times and to use security at multiple layers. Use unlike methods to limit SSH access to your servers, or use services that volition block anyone who tries to use animate being force to proceeds access to your servers. Fail2ban is ane example of such service.
VNC Over SSH
For users who are used to working in a graphical desktop environment with Virtual Network Computing (VNC), information technology is possible to completely encrypt connections using SSH tunneling. In order to tunnel VNC connections over SSH, you will demand to run this command in the terminal on your Linux or UNIX machine:
$ ssh -L 5901:localhost:5901 -Northward -f -l username hostname_or_IP Hither is the breakdown of the command to a higher place:
- ssh : this starts the SSH client program on your local motorcar and enables secure connection to the SSH server on a remote estimator.
- -L 5901:localhost:5901 : states that the local port for the client on the local automobile is to exist forwarded to the specified host and port of the remote machine. In this case, local port 5901 on the local client is beingness forwarded to the same port of the given remote server.
- -Northward : instructs to just forrad ports, and non to execute a remote command.
- -f : sends SSH to groundwork after the countersign is provided, just before the command is executed. Then, you can freely utilise the terminal to blazon commands on the local automobile.
- -l username : the username yous insert here will exist used for logging in to the remote server you specified.
- hostname_or_IP : this is the remote organisation with a VNC server. An example of an IP address would be 172.16.0.five and the example of a hostname would exist myserver.somedomain.com.
You can besides connect to a remote server via SSH tunnel from a Windows machine past using PuTTY. In the PuTTY configuration window:
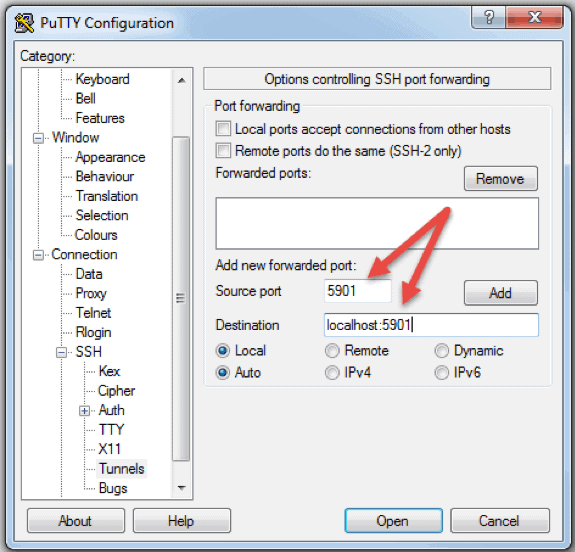
- Go to Connection -> SSH -> Tunnels
- In the Source port field blazon in 5901
- In the Destination field blazon in localhost:5901
- Start the SSH session equally you normally would.
- Connect to your server with a VNC client of your choice.
What is RDP?
Remote Desktop Protocol (RDP) is a protocol adult by Microsoft. Information technology is used to command and manage machines with a Windows operating organization remotely.
Unlike Secure Crush, connections established using an RDP client provide a user with a graphical interface through which they can gain access to a remote computer and command information technology in the same manner as their local computer.
Using Remote Desktop services, formerly known equally terminal services, allows network and system engineers to easily manipulate remote computers connected to a local network or the Net.
This comes with a price. If you do not employ a virtual individual network (VPN), connecting via RDP is far less secure than SSH because you are directly exposed to the internet. In that location are many automatic scripts constantly looking for weaknesses in your connectedness, especially for open ports that Windows Remote Desktop connections employ. In that case, it is highly recommended to have strong, secure passwords and change them regularly. This does not make RDP connections safe, merely less vulnerable.
How Does Remote Desktop Protocol Piece of work?
Windows Remote Desktop connectedness is based on a rather unproblematic customer-server model using Remote Desktop Protocol (RDP). After you enable it, the Windows Remote Desktop server-side service starts listening for connection requests on port 3389. Whenever you attempt to connect to a Windows server, you volition need to provide a valid username for the account y'all are using to gain access remotely. One time you gain admission to the server, you volition be able to manage applications, transfer files between the 2 computers, and nigh perform any job you lot tin perform locally with the business relationship in question.
No thing what version of the Windows operating system you have, you volition exist able to constitute a secure remote connectedness to some other computer since the Remote Desktop client is available by default. On the other hand, a reckoner can be remotely attainable simply if it runs on a Pro, Enterprise, or Server edition of a Windows operating system. Then, we can conclude that RDP connections are possible only between computers with a Windows OS on them.
How to Enable an RDP Connection
Establishing a Remote Desktop connexion to another computer over network requires you to enable the Windows Remote Desktop server service. The Remote Desktop client is integrated into Windows systems, set out of the box, and does not demand whatever special setup earlier you can connect to another Windows-based auto. Still, accepting Remote Desktop connections from another machines is disabled by default on all version of Windows Bone.
If you want to remotely connect to a server over the Internet and not through the local network, you demand to take a few things into consideration before you enable this service:
- Port forwarding. If you are not using a VPN you need to brand certain the ports are forwarded properly to the remote host'due south IP accost. Check the router settings to see if the traffic on the default TCP port for Remote Desktop Protocol (port 3389) is going to the IP of the server with which you lot want to establish a Remote Desktop connection. Note that your Windows server is in this case directly exposed to the Internet and vulnerable.
- Using a VPN. This is a much safer choice for Remote Desktop connection. When yous create a virtual private network on a customer reckoner, you volition be able to access all services that are available only when you use local connexion.
- Firewall settings. Brand sure that the firewall you are using for the remote machine is not blocking Remote Desktop connection. You need to open up the local port for RDP, whether it is the default or custom port number.
Enabling Remote Access in Windows vii, 8, 10 and Windows Server Versions
The procedure to configure remote desktop and allow secure remote connections to a server or a PC from a unlike computer is similar for all versions of Windows operating systems. I volition list the basic steps to enable remote access to a desired machine. Before yous begin, delight brand sure that you have taken into consideration the notes listed above concerning port forwarding, VPN, and firewall settings.
Footstep ane: Allow Remote Connections
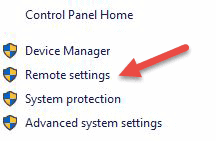
Go to the reckoner information on the machine where y'all want to permit remote connections:
- Right Click on Estimator or This PC depending on the Windows OS version.
- Click on Properties.
- Click on Remote settings on the left side of the window.
- Click on Allow remote connections to this figurer. This should automatically add together Remote Desktop Firewall exception. Additionally, you can check off the box that says "Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)" for additional security of your RDP sessions.
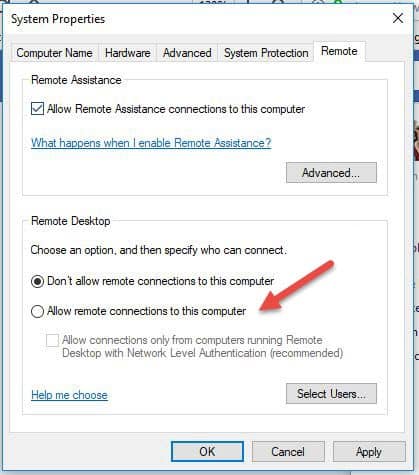
- Click Employ if you lot want to stay in the tab or OK to close information technology.
Step 2: Add Users to the List of Remote Users
You need to perform this step only if you want to allow users other than administrators to access the automobile in question. If y'all are an ambassador, your account is automatically included in the list of immune users but yous will not meet it. To select more users:
- On the Remote settings screen shown above, click Select Users…
- Click on Add together in the Remote Desktop Users box.
- The Select Users box will appear. You can select the location you want to search by clicking on Locations.
- In the Enter the Object Names to Select field, type a name of a user and click on Check Names.
- When you find a friction match, select the user business relationship and click OK.
- Close the System Backdrop window past clicking OK once again.
At that place are not many other options to change in order to configure Remote Desktop. Provided that other settings do not interfere with your Remote Desktop connectedness, yous are now able to remotely connect and control this reckoner.
How to Employ the Remove Desktop Connection Client
Using the Remote Desktop customer is straightforward and you practise not need to specifically configure Remote Desktop on the local computer. The steps beneath volition piece of work for all versions of Windows starting from Windows seven.
Pace i: Launch the Destkop Connexion Unit of measurement
On your local Windows estimator, locate the Remote Desktop Connexion awarding. You can notice information technology in a couple of dissimilar ways:
- For Windows 7, click on Start -> All Programs, go to the 'Accessories' folder and click on Remote Desktop Connexion. For Windows 10, Click on Start and locate the 'Windows Accessories' folder where y'all tin also observe the Remote Desktop Connection app.

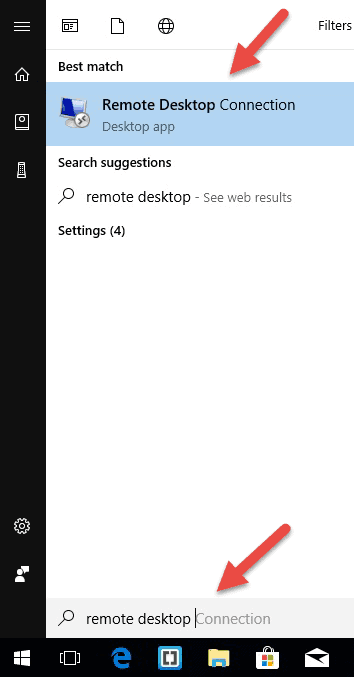
- Click on Start and type in Remote Desktop Connection in the search bar. Yous will receive search results as shortly as yous start typing. Click on the application when it shows upwards on the list.
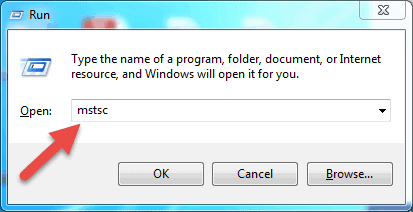
- Printing Windows + R keys on your keyboard to get the "Run" box. Blazon in mstsc and hit Enter in the 'Open:' field to run the Remote Desktop client.
Step 2: Enter the Remote Hosts IP Accost or Name
Once y'all launch the Remote Desktop Connexion awarding, you will get a window where you can enter the name or the IP address of a remote machine y'all want to access.
In the Reckoner field, type in the corresponding proper name or IP address and click Connect.
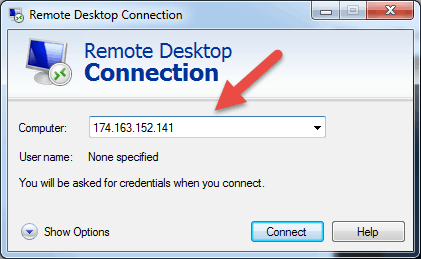
Note: If the default listening port for Remote Desktop connection (port 3389) has been inverse on the remote host to a different value, y'all will have to specify it after the IP address.
Example: 174.163.152.141:6200
Depending on your circumstances, you will either need to enter the private or public IP address of the remote host. Hither are the possible scenarios:
- If the client computer and the remote host connect to the same Local Area Network, you volition use the host's private IP accost for Remote Desktop Connexion.
- If you are using a virtual private network (VPN) on the client computer to admission the remote host, you will utilize the host's private IP accost for Remote Desktop Connection.
- If the customer computer is connecting to the remote host from some other network over the Net without a VPN, y'all volition use the public IP address.
How to Find the IP Address and Host Name
In that location are many ways to locate the name, public or private IP address of a estimator where you want to configure Remote Desktop service. Hither are the quickest and easiest methods:
To make up one's mind a computer's private IP address:
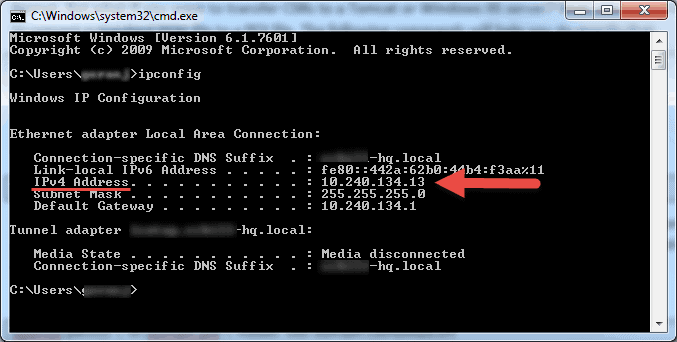
- Search for CMD from the get-go menu or press Windows + R on your keyboard, blazon in CMD and hit Enter to run the command prompt.
- Type ipconfig in the command prompt and hit Enter.
- Your volition run across your calculator's individual IP accost nether the IPv4 Address line.
To determine which public IP accost a reckoner is using:
- From your web browser, go to com or utilize its search bar.
- Blazon in "what is my IP" or merely "my IP" and hit Enter.
- At the pinnacle of the page, Google will prove you the public IP address your figurer is using. If this is not working for your region, you can visit the starting time webpage in the search results and it will show you the IP address. Some websites such equally world wide web.whatismyip.com will even testify you your individual (local) IP address.
To find a reckoner's name:
- Right Click on Computer, or This PC, depending on the Windows OS version you are using.
- Click on
- You volition find your full reckoner proper name under the "Computer name, domain, and workgroup settings" section.
Step 3: Entering the RDP Credentials and Finalizing the Connection
After you lot hit connect, the loading bar will appear. When it finishes initiating and configuring the remote session y'all will get a pop-upwardly window that will look like to this:
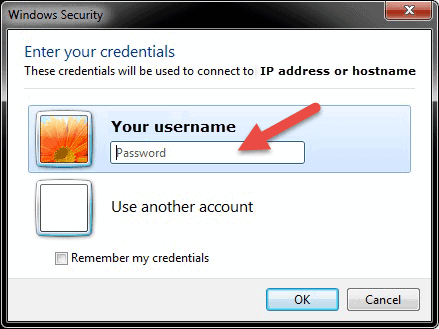
- Enter the password for the selected username. You can apply another business relationship, if needed, and provide a different username and countersign.
- Click OK when ready and y'all will get the security certificate warning.
- Click Aye to continue.
Note: Only i user can exist logged in at the same fourth dimension on a Windows estimator. If someone else is using the auto yous are trying to remotely admission, that user has to disconnect. The warning logon message will appear in such cases.
You will not see the desktop of the remote motorcar. Depending on the user account permission settings, you can now perform any performance that you can while working direct in front of it.
Remote Desktop Protocol Further Steps
When setting up your remote server or automobile to accept remote desktop connections, it is important to take precautions concerning securing RDP. Your server is specially vulnerable if you are accessing it over the Internet.
Here are a few pieces of communication to keep in listen if y'all are using remote desktop protocol to remotely connect to your machines:
- Use the congenital in VPN server on your Windows machine to additionally secure your traffic. This volition provide more secure access to your Windows server and services.
- Set client connection encryption level. This option is fix to "Not configured" by default. Y'all can enable it and strength high encryption level settings for all communications between clients and Remote Desktop Session Host servers. We exercise not recommended using the "Customer Uniform" encryption level setting. Leaving the default "High" encryption level setting volition forcefulness strong 128-chip encryption for data sent from the client to server and vice versa. You lot can edit this configuration using the Local Grouping Policy editor.
- Employ two-cistron hallmark using a tertiary-party tool, such as Duo Security. By installing Duo Authentication for Windows Logon, you tin add ii-gene authentication to all Windows login attempts, or only for RDP sessions.
- Enforce firewall rules to limit exposure of open up RDP ports to the Cyberspace, especially if you lot are using the default RDP TCP port 3389. Windows has a built-in firewall which you can access from Control Console and further configure it to restrict traffic to specific ports and IP addresses
These best practices for additionally securing RDP will help y'all tighten down remote desktop admission. You will avoid most of the unauthorized login attempts without spending as well much fourth dimension making configuration changes to your machines.
Annotation: Larn how to use SSHFS to mount remote file systems over SSH.
Conclusion
The steps and processes listed in this guide will work for most users and almost versions of Linux and Windows operating systems.
You should now be able to Connect to a Remote Server with Linux or Windows.
There are of course many other methods to establish a connectedness betwixt ii remote computers, but the ones covered here are most common.
Was this article helpful?
Yes No
Source: https://phoenixnap.com/kb/ssh-to-connect-to-remote-server-linux-or-windows
Posted by: smithsuand1943.blogspot.com

0 Response to "How To Ssh To A Server From Windows"
Post a Comment